| Get Ready for Expanded Pwn2Own 2017 |
| Written by Alex Armstrong | |||
| Thursday, 19 January 2017 | |||
|
This year's Pwn2Own hacking contest will be the 10th anniversary edition and the first to be entirely run by Trend Micro. It will feature more targets and more prize money for security researchers who successfully execute zero-day exploits. As reported last March in Pwn2Own 2016 - The Results last year's contest was held under the joint auspices of Hewlett Packard Enterprise and Trend Micro, following Trend Micro's acquisition of HPE's Tipping Point division. By the end of the two-day event, which is held annually in conjunction with the CanSecWest conference, researchers had successfully exploited a total of 21 bugs and a total of $460,000 USD bounty paid out to participating teams and individuals. Commenting on 10 years of the contest. Brian Gorenc, who has been with ZDI since 2012 and moved from HPE to Trend Micro where he is now Senior Manager, Vulnerability Research and responsible for organizing and adjudicating Pwn2Own, blogged: The first Pwn2Own happened before Conficker or Stuxnet. It happened before the rise of nation-state attacks. It happened before the explosion of ransomware. It happened before the explosion of cloud computing. It happened before bitcoin. It happened before anyone had ever heard of the Internet of Things. In other words, a lot has changed since 2007, including Pwn2Own. That first year, a laptop and $10,000* were given away. Last year, more than $450,000 cash and prizes were awarded over the multiple categories. In 2007, a single bug was needed to exploit QuickTime. Last year, a chain of bugs was required to complete a compromise and fully win a category.
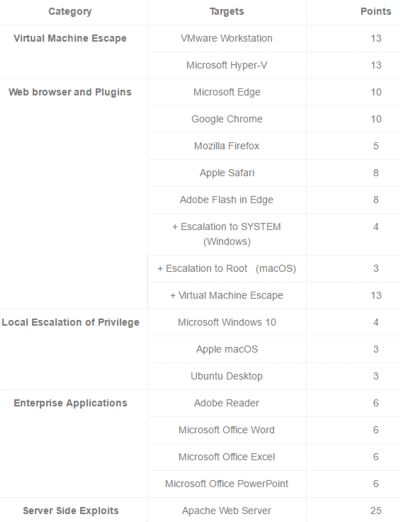
Up to $1,000,000 in prizes will be available in this year's contest taking place in Vancouver on March 15-17 and there are some interesting additions to the lineup with Linux being included as a target for the first time for escalation of privilege bugs, which now have a dedicated category. Contestants who successfully take advantage of a kernel vulnerability to escalate privileges will earn $30,000 for Microsoft Windows 10, $20,000 for macOS, and $15,000 for Ubuntu Desktop. A category for Virtual Machine escape was added last year and this is being expanded to Microsoft Hyper-V as well as VMWare. A successful exploit in either product will win $100,000. One new category for this year's contest is Server Side in which a successful exploit against Apache Web Server on Ubuntu Server, launched from the contestant laptops within the contest network, will net the researcher $200,000. Brian Gorenc comments: Considering this setup accounts for roughly half of all websites, it’s pretty clear the impact a bug here would have. Exploits against Adobe Reader and Microsoft Office (Word, Excel and PowerPoint), worth $50,000, are now introduced in the Enterprise Applications category. According to Gorenc: These types of exploits are seen in the wild quite a bit, so shutting a few down could really help improve the security posture for a lot of folks. Firefox, which was dropped from last year's contest, is back although with a lower payout, $30,000, than browsers that are more secure. Edge and Chrome are both worth $80,000 with Safari and Adobe Flash in Edge, $50,000. Contestants in the Web Browser and Pugins category can earn an additional $30,000 if their entry achieves SYSTEM-level code execution on Windows-based targets, or an additional $20,000 if their entry achieves root-level code execution on macOS-based targets. Gorenc advises: Want a really big payout? The Windows-based targets will be running in a VMware Workstation virtual machine. If the contestant escapes the VMware Workstation virtual machine and achieves code execution on the host operating system, the contestant will receive an additional $100,000. These are cumulative bonuses, as well. For example, if a contestant exploits Google Chrome or Microsoft Edge, elevates to System, then performs a VMware escape, they will net themselves a tidy $210,000 in one sitting (and 27 Master of Pwn points!). We certainly hope someone accomplishes some chain along these lines. The Master of Pwn award, introduced last year for the researcher who had the best overall performance, is back this year. It uses the following points system where the number of points reflects the difficulty of the exploit:
The contestant with the highest total points will receive the title “Master of Pwn” and receive 65,000 ZDI reward points (estimated at $25,000) and is likely to be able to show off in a smoking jacket like the one won last year by Tencent Security Team Sniper.
Advance registration is required for Pwn2Own with a deadline of March 12 at 5:00 p.m Pacific Time. Potential entrants are encouraged to read the contest rules thoroughly before registration.
More InformationPwn2Own Returns for 2017 to Celebrate 10 Years of Exploits Related ArticlesLargest Payout Ever At Pwn2Own 2015 To be informed about new articles on I Programmer, sign up for our weekly newsletter, subscribe to the RSS feed and follow us on Facebook or Linkedin.
Comments
or email your comment to: comments@i-programmer.info
|
|||
| Last Updated ( Thursday, 19 January 2017 ) |