| The Discovery Of The Twitter Bursty Botnet |
| Written by Lucy Black | |||
| Friday, 22 September 2017 | |||
|
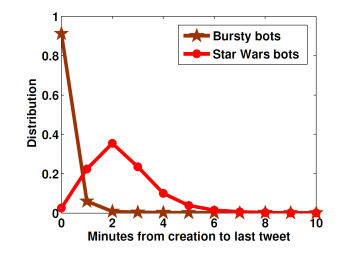
There is no doubt that bots are a growing problem, but perhaps it is a bigger problem than any of us imagine. Researchers have discovered a Twitter botnet with over 500,000 bots, and it isn't a simple one. Juan Echeverria, Christoph Besel and Shi Zhou of University College London have been working hard to identify bots, but I doubt that even they imagined that their latest discovery actually existed: "Many Twitter users are bots. They can be used for spamming, opinion manipulation and online fraud. Recently we discovered the Star Wars botnet, consisting of more than 350,000 bots tweeting random quotations exclusively from Star Wars novels. The bots were exposed because they tweeted uniformly from any location within two rectangle-shaped geographic zones covering Europe and the USA, including sea and desert areas in the zones. In this paper, we report another unusual behaviour of the Star Wars bots, that the bots were created in bursts or batches, and they only tweeted in their first few minutes since creation. Inspired by this observation, we discovered an even larger Twitter botnet, the Bursty botnet with more than 500,000 bots. Our preliminary study showed that the Bursty botnet was directly responsible for a largescale online spamming attack in 2012. Most bot detection algorithms have been based on assumptions of ‘common’ features that were supposedly shared by all bots. Our discovered botnets, however, do not show many of those features; instead, they were detected by their distinct, unusual tweeting behaviours that were unknown until now." The Star Wars bot net was easier to spot because of its geographical localization but it doesn't fit into the expectations of what a bot is. The fact that they only tweeted in the first few minutes of being created - bursty tweeting.
This was used as a new characteristic to test for other bots and this is how the Bursty botnet was discovered. The characteristics of this new botnet are: • They were registered in February and March 2012 with user IDs between 5 × 108 and 5.35 × 108 • They show bursty tweeting behaviour. That is, they generated at least three tweets and they only tweeted in the first hour after their creation • They only tweeted from the source of ’Mobile Web’ • They mostly tweet (i) a URL; or/and (ii) a mention of another user. It also seems that Twitter knows about at least some of the users as 300,000 users identified as part of the Bursty botnet in 2015 were removed in 2016. However, this still leaves a large number of bots still active. So why bother? "It is almost certain that the Bursty botnet was carefully designed and centrally controlled for the purpose of a spamming attack. A number of tricks have been used to hide the attack. Firstly, the bots were created in large numbers, and each bot was used to generate a small number of tweets in the first few minutes only and then the bots all became silent. Most existing bot detection methods are not able to identify such inactive bots. Secondly, the bots used a complex network of URL shorteners and redirects to obfuscate the final landing pages, such that the vast number of URLs were used only once, which could effectively evade most spam filters. Also it was not easy for users to tell on the final destination of the URLs. Thirdly, the botnet directly targeted over 1.3m distinct Twitter users by mentioning their usernames, which significantly increased the chance of the URLs being clicked. Our analysis revealed just how successful this technique was: pn average over 61% of the posted URLs that lead to a phishing campaign were clicked, which could yield a remarkable revenue by selling stolen personal data. With the above information and further research, we were even able to track down the alleged botmaster of the Bursty Botnet. Our detailed analysis on the spamming attack of the Bursty botnet will be published in another paper." |
Ruby 4 Adds Ruby Box On Its 30th Anniversary 08/01/2026 Ruby 4 has been released with new features including a new just-in-time compiler called ZJIT and an experimental sandbox called Ruby Box. The new version also adds features to the experimental pa [ ... ] |
Humanoid Alpha Learns To Wrap Xmas Presents 26/12/2025 If you've been cursing the sticky tape and searching fruitlessly for the scissors, maybe a robot is the solution. The team behind the Humanoid HMND 01 Alpha Bipedal certainly thinks so. The compa [ ... ] |
More News
|