| The Memory Principle - Computer Memory and Pigeonholes |
| Written by Mike James | ||||
| Thursday, 07 January 2021 | ||||
Page 2 of 3
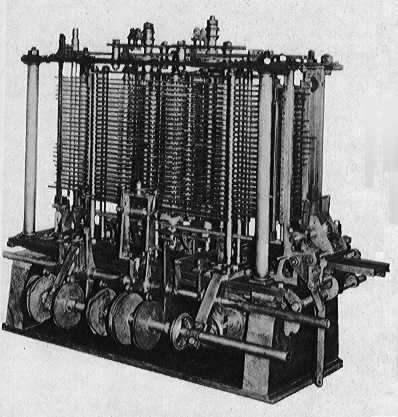
I left the lecture in a state of shock and stumbled home. I don’t think I recovered from the idea for many months and certainly Fortran programming was never the same again – possibly to this very day. Now my guess is that you are probably thinking that my shock was due to thinking that they kept pigeons in computers? No, that wasn’t it at all. The real source of my trauma was that I could see that a set of pigeonholes could be described as a memory that things could be stored in and retrieved from. I could also see that my school bag fulfilled the same role. I could also see that if I left a light on in a room it “remembered” the fact that I had done it. All of these esoteric ways of looking at the obvious did nothing to help me understand how computers, and computer memory in particular, worked. Yet the man who knew clearly thought it did, it should and it would. To him the picture of a set of pigeonholes clearly represented the functional principle of a computer memory - but to me it was just a set of pigeon holes and how it could ever be part of something larger was, and still is, a mystery. There really is a bigger idea here than storing pigeons. After a spending the intervening years thinking about why the pigeonhole model of computer memory just didn't work the answer was presented to be courtesy of Babbage and his wonderful machine. When Babbage moved on from his Difference Engine, which is best described as a special purpose calculator, to his real computer, the Analytical Engine, one of the things he invented was the “memory principle”. People had used pigeonholes before to store and retrieve things but this didn't mean they had invented computer memory. Babbage’s machine needed to store decimal numbers and the first part of this problem is easy to solve by anyone familiar with the pigeonhole. All he did was to take a stack of wheels and the number stored in his memory location is given simply by the position of the wheels – the units wheel, the tens wheel and so on. By having more than one stack of wheels his machine could store more than one value. If you call the first stack A, the second B and so on then storing and retrieving numbers is just a matter of saying “store 10 in A”, “retrieve the value in C” and so on. You can see that just like the pigeonholes each memory location has an address, A, B, C and so on and a stored value.
The analytical engine has no pigeons - anywhere.
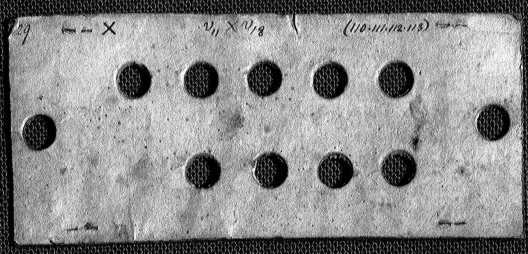
An early punched card
This is where the account of computer memory usually stops and hence why pigeonholes and other such simple analogies are often used to explain it. However, it leaves out perhaps the most important feature of a computer memory that makes it different and so much more than a set of pigeonholes. The Memory PrincipleTo understand the memory principle it we have to go back to my six-line Fortran program and think a little about how it might work. Well actually Fortran is a little advanced. What we really need is machine code and we might as well use Babbage’s. His machine stored instructions on punched cards as a pattern of holes. Each card was a single instruction. Now consider a card that holds the instruction: Store 10 in B This looks superficially like the instruction to place a pigeon in a particular hole but it is more than this. The holes punched in the card not only mean “Store 10 in B” they actually DO IT. Imagine that resting on the card is a set of rods. Where there is a hole the rod goes through and so moves. The movement of rods into and out of holes is what sets the machine up to do a particular operation and it selects the stack of wheels that the number will be stored in. In the case of “Store 10 in B” the holes that specify wheel stack B will let rods drop through that physically move it into position so that it's, and only it's, cogs engage with a gear wheel. The holes that specify the “Store” operation will set the machine up so that gear wheel is driven by the processor and the rods that specify 10 arrange that it will rotate exactly ten times. I’m going to leave it to your imagination to work out how the last piece of machinery could be implemented but you should be able to see that it is possible. Also notice that the number stored is in fact added to the wheel stack rather than just transferred. It turns out in most computer implementations to be easier to add a value than store it. As long as the programmer remembers to clear, i.e. set to zero, the location before adding this is equivalent to a store operation. This is the reason that some specialised memory locations where arithmetic was performed were, and still are, called “accumulators” - they sum up or accumulate all of the numbers stored in them. If you want to work out the details of how a “Load A from B” operation might work I’m sure you will see that retrieving data from B is just a matter driving the cog wheel in the opposite direction until the value stored in B is reduced to zero. Of course the same cog wheel could be arranged to drive wheel stack A in the positive direction so adding what was stored in B to A. A “Subtract A from B” instruction could be… Stop! This is getting much to detailed. I have no intention of building the Analytical Engine and we are in danger of missing the point. What is important is that you can see that computer memory isn’t like a set of pigeonholes. It has addresses and storage locations like a set of pigeonholes but in the case of computer memory the addresses aren’t just static labels. Computer memory addresses actually do select the memory locations they address and this is very different to just having pigeonholes with labels. It is much more like having a bank of pigeonholes that are all covered by doors. In this case the instruction to store a pigeon in hole 1234 would automatically cause that pigeonhole door, and no other, to open. The pigeon would then fly into the waiting memory location. The instruction to retrieve the pigeon from location 1234 would again cause just that door to spring open and the pigeon would fly out. I’m sure that you can imagine some wild and wonderful Heath Robinson or Rube Goldberg style mechanical machinery to automatically store and retrieve pigeons – and I wouldn’t dream of denying you this pleasure! The key point is that in a computer memory the addresses are not just dead and static labels for locations they are active selectors. A computer memory is a mechanism where presenting the address returns the contents of the memory or allows something to be stored there. How does all this relate to today’s modern computer? Surprisingly well, as it turns out. |
||||
| Last Updated ( Thursday, 07 January 2021 ) |