| Codebreaking and Colossus |
| Written by Historian | ||||
Page 2 of 3
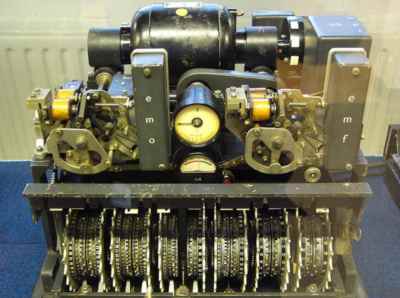
Lorenz/Tunny codesThe story of the early electronic computing device that was used in code cracking really concerns the more sophisticated coding machine, referred to as both "Tunny" and "Lorenz". It was an automatic teletype system that carried much of the German high command's communications.
A Lorenz coding machine These teletypes transmitted data using a five-bit code read from a punched paper tape. The transmission was fast and convenient in the sense that the paper tape could be punched using a standard keyboard and the reception of the message automatically produced a paper listing. Fast it may have been but without some type of encryption it would be very vulnerable to interception. The Enigma machine could have been used to encode and decode the messages but as this was a manual machine it would have slowed things down a great deal. A better solution was to build the encryption hardware into the teletypes being used. The Lorenz SZ42 cipher used in the teletype machines was based on the "one time pad" invented by Gilbert Vernam. The basic idea was that each bit of the teletype code is added mod 2 to another bit which plays the role of a key. To code a complete message you need a second tape - the key tape - which has as many characters as the message tape. The two tapes are then run through tape readers at the same time and each pair of characters is added together mod 2. The result of the addition is then transmitted as the encrypted message. To de-encrypt the message all you have to do is repeat the process but this time each character on the key tape is added to the encrypted message to produce the original text. Notice that for the system to work both the sender and receiver have to have a copy of the key tape and this has to be as long as the original message. There is also the problem of what the key tape should actually be. If the key tape is really random then it turns out that the code is virtually uncrackable. Indeed if the key tape is truly random then the encrypted message also looks as if it was truly random and hence contains no regularities that can help the code breaker. Clearly the one time pad is an excellent code but for the twin requirements that it have a key as long as the message and one that has to be known in its entirety by the sender and the receiver. A simple modification is to replace the key tape by a pseudo random number generator and this is exactly what the German cryptographers did to encode their teletype messages. A system of mechanical disks were used to generate a complex binary sequence that looked complicated enough to look random. The sequence that was generated only depended on the setting of a number of in/out pegs on each wheel. You can think of this as a "seed" that specified the start of the pseudo random sequence. Of course this simplicity was bought at the expense of a less than perfect encryption. As the key sequence was only pseudo random there were still patterns and regularities in the encrypted text that a code breaker could make use of. The Bletchley Park cryptologists, who included Bill Tutte and Max Newman had determined that, as a first step, a special key tape had to be tried against a received message in every possible starting position. At first the solution seemed obvious. All that was needed were two paper tape loops. One would consist of the message and the other the probe key. The two loops would be run together in sync and the mod 2 sum of each character formed by electronics. Each time round the two loops would shift by one character until all possible combinations had been tried out. Easy? Well yes as long as you can figure out a way of running the tapes at high speed. This proved to be very difficult because of the need to use sprocket holes to keep the two tapes in sync. Tommy FlowersAt this point the Post Office and Dollis Hill enter the scene in the guise of Tommy Flowers. He was an engineer who was well in touch with the electronics of the time and . The son of a bricklayer in the East End of London, Flowers completed an apprenticeship in mechanical engineering at the Royal Arsenal, Woolwich. While doing this he took evening classes at the University of London to earn a degree in electrical engineering. He joined the telecommunications branch of the GPO (General Post Office) in 1926 and in 1930 moved to work at the research station at Dollis Hill, was involved in all areas of communications including telephones and radio. At Dollis Hill Flowers had proved to his own satisfaction that any electro-mechanical switching system can be replaced by valves.
Tommy Flowers (1905-1998)
Tommy Flowers was initially invited to Bletchley Park to build a decoder for the relay-based Bombe machine developed by Turing to help decrypt the Germans' Enigma codes. Although the decoder project was abandoned, Turing was impressed with Flowers's work, and in February 1943 introduced him to Max Newman who was leading the effort to automate part of the cryptanalysis of the Lorenz cipher. To meet the need for a machine to automate the tape matching that had hitherto been done manually Flowers and Frank Morrell (also at Dollis Hill) initially designed a machine that was nicknamed the Heath Robinson due to its resemblance to the crazy machines thought up by the renowned British cartoonist of that name.
Replica of Heath Robinson at TNMOC
The Heath Robinson successfully proved the concept but it still took far too long. Then Tommy Flowers realised that the whole problem of synchronisation of high speed tapes could be avoided by getting rid of one of the tapes! How? Simple just store the bit pattern in the probe key tape in a semi-permanent memory, add some fast electronic mod 2 addition hardware and there you have Colossus - a valve based computer built two or three years before ENIAC. (In fact the first Colossus was finished the year work started on ENIAC.) (Tommy) Flowers Close with one of the research station buildings behind - now a residential development. |
||||
| Last Updated ( Monday, 27 November 2023 ) |