| Using Microsoft Network Monitor 3.3 |
| Written by Mike James | ||||||
| Wednesday, 31 March 2010 | ||||||
Page 2 of 2
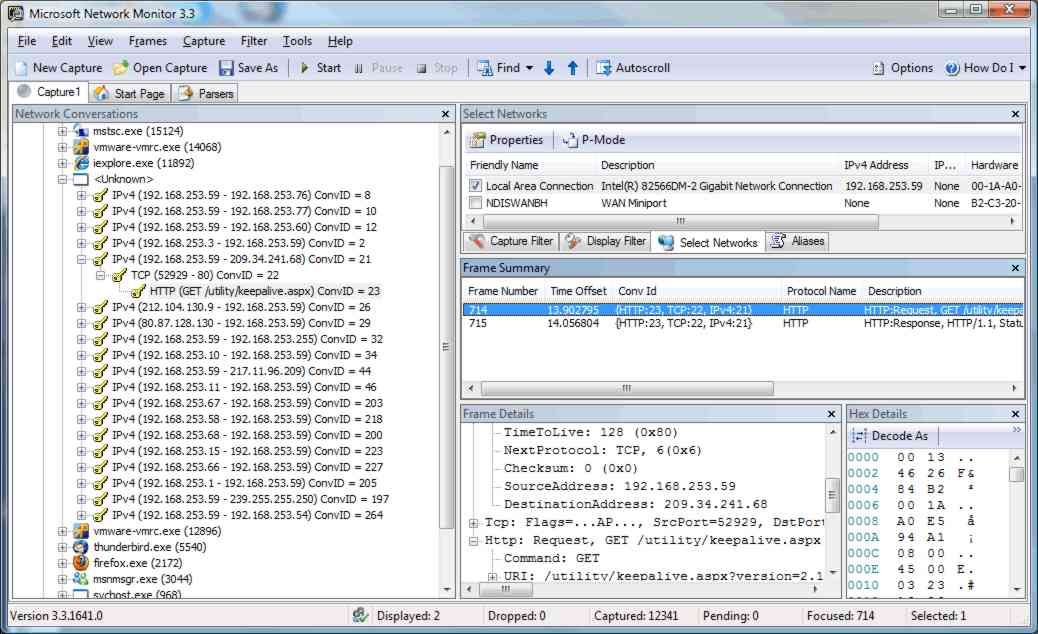
The only way to gain an idea of what a network conversation is all about is to expand the node in the tree and take a look at who is talking to whom and what sort of conversation is going on. For example, if you expand the Unknown node you can immediately see the IP addresses of each of the machines involved in each of the conversations. In general any conversations going on between a pair of machines internal to your network isn't going to be an indicator of anything strange going on - they could be but most malware is concerned with communicating with the outside world.
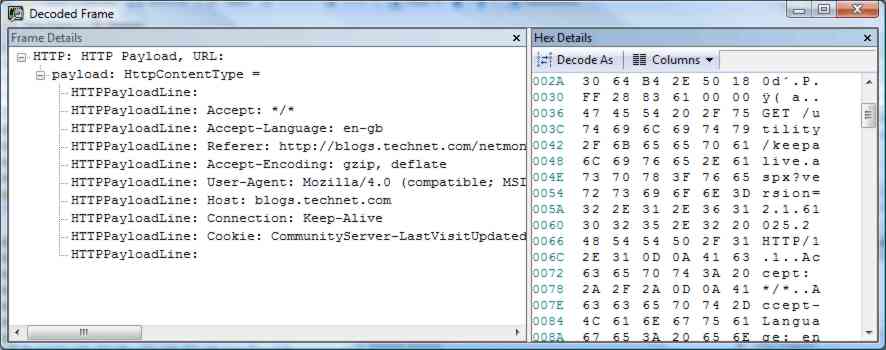
Looking for external IP addresses Scanning down the list reveals that there is a conversation going on between the machine being monitored and the outside world. Expanding that node reveals that it is a TCP conversation. Expanding the tab further reveals that there is an HTTP conversation between the same two addresses and that this is to a "keep alive" page. This means that the conversation is probably OK but to check further you can select the HTTP conversation and have the frame decoded in the "Frame Details" windows. This extracts the basic data from the frame and decodes it so that you can read the various fields. However, we know that this is an HTTP frame and we could extract even more information. To do this simply click the Decode As button in the Hex Details window and select HTTP from the list that appears. You can do this quickly by typing H and then T. From the decoded data you can easily see that the conversation was about a keep alive heartbeat with a known and trusted website and the only payload of any importance is a cookie - which is presumably OK.
Decode the data in the frame Now you have seen some of the basic capabilities of the network monitor. It can collect all the data passing to and from the monitored machine. You can look at conversations and find out the source and destination IP addresses and you can examine a particular packet and the data it contains. As long as you know the protocol in use you can even decode the packet and see what it contains in plain English. The monitor comes with a lot of standard protocol decoders and it is possible to write more. This is just the start, however. You can set up filters that remove all of the traffic you are not interested in and you can focus on anything out of the ordinary. It is also possible to load experts which will perform standard analysis on the data you collect. Follow the lnks above for articles on each of these topjcs. Finally notice that you can save the data you have captured and subject it to more complex filtering, charting and decoding. The network monitor gets you inside your network.
<ASIN:0132236931> <ASIN:0596008406> <ASIN:0321492668> |
||||||
| Last Updated ( Sunday, 09 May 2010 ) |