| Simplify PostgreSQL Database Access With Neon Authorize |
| Written by Nikos Vaggalis | |||
| Monday, 30 December 2024 | |||
|
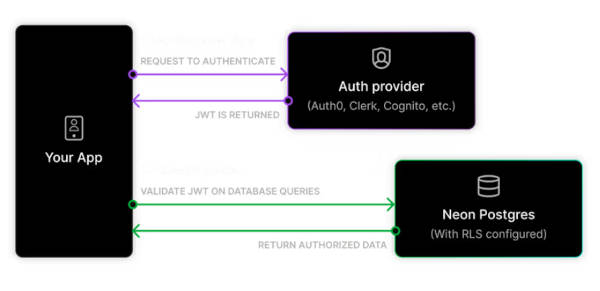
By fusing PostgreSQL native row-level security The key concept to take away is that Neon handles the authorization part; the authentication part of managing user identities, passwords, and security tokens is still handled by third-party JWT-based authentication providers like Auth0 and Clerk. What Neon does is integrating that external authentication with the internal authorization required by the database in order for a user to access his own underlying rows, by extending PostgreSQL's native Row Level Security. Let's see an example in action by enabling RLS on a table called 'departments' : ALTER TABLE departments --Next we create the policy CREATE POLICY department_managers Now you no longer have to write application level queries such as select * from departments as this is handled by the database itself automatically and as such select * from departments issued by Alice can retrieve only her rows and no one else's. Of course for it to work you have to authenticate/ log the user in the user by any means necessary, so that current_user becomes 'Alice'. With Neon Authorize this process goes a step beyond. Since nowadays most applications authenticate with the use of JWTs, that JWT is passed on to Neon which then can make use of the validated user identity directly in Postgres. To facilitate the integration with an authentication provider, you will have to add your provider's JWT discovery URL to your Neon project. This lets Neon retrieve the necessary keys to validate the JWTs: As such, when your code calls: const sql = neon(process. env. DATABASE_AUTHENTICATED_URL, { authToken: myAuthProvider. getJWT() }); this derives the user id from the token, which Neon's open source pg_session_jwt extension makes it available to Postgres for RLS to take place.
Furthermore, you’ll also have access to a few utility functions such as auth. session() and auth.user_id() which will help you use the JWTs that are coming from your auth provider, like : SELECT At the time of writing Neon Authorize is compatible with the following Auth providers:
but that list keeps expanding. With that in place we can remove access control from the application layer to rely solely on RLS at the database level You can run Neon locally or if you prefer cloud managed then you can start right away with the free offering for up to 10 projects and upgrade later if necessary. There's also a good tutorial to get you started, which uses Clerk as the authentication provider. More InformationAbout Neon Authorize Related Articles
To be informed about new articles on I Programmer, sign up for our weekly newsletter, subscribe to the RSS feed and follow us on Facebook or Linkedin.
Comments
or email your comment to: comments@i-programmer.info |
|||
| Last Updated ( Monday, 30 December 2024 ) |