| Fluid Passwords - Never The Same Password |
| Written by Mike James |
| Friday, 08 September 2017 |
|
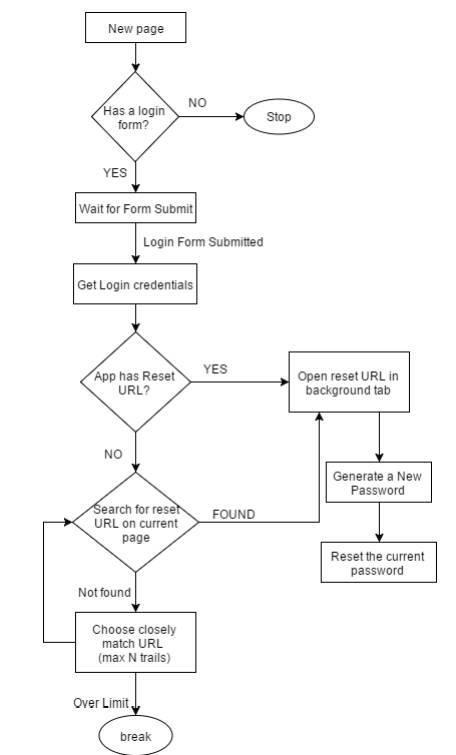
Despite lots of predictions that passwords are on their way out, they still form the basis of most security. The problem is that even with strict rules about changing them, passwords tend to persist for too long. Now a clever idea makes it possible to keep passwords fluid. The problem with passwords is that once stolen they generally remain useful for some time - passwords aren't changed often enough. Now some creative engineering from the University of Oklahoma provides a workable solution. The idea is to simply automate password changing: We propose an effort-free, client-side solution to the problem of password theft in the form of a Firefox add-on to automate password resets, which we call Fluid Passwords. The idea behind our add-on is: for a given website, after a user logs in, seek out the site’s password reset page, generate a secure random password, and update the password for the account. By leveraging Firefox’s built-in password manager, we can then store the updated password for use at the next login, all without requiring any interaction from the user. By leveraging Firefox Sync, users can access both their stored passwords and the add-on on any computer they login with, effectively reducing the number of passwords any one person has to remember to the one they use for Firefox Sync. The big problem is finding and using the password reset. Most sites have security measures on signup pages to ensure that the user is human, but password reset pages are nearly always unprotected in this way because the user has already validated using the password. Even so, password reset pages vary a lot. The team worked out an algorithm to find and use reset pages:
The add-on opens a background tab and tries various reasonable URLs in an effort to find the password reset page. Once found it generates a pseudo random 12-character string to use as the new password. Notice that, as Firefox is being used as a password manager, the memorability of the password doesn't matter. The address of the password reset page is stored so that next time the site is visited there is no need for a search. The add-on was tested on 29 of Alexa's top 100 websites. Sites were excluded for all sorts of reasons - security is not simple or uniform. For example, the main Google log in was not tested because changing its password would mean all Android devices using the same account would have to update their passwords as well. Some sites also ask a security question and the program couldn't cope with these and, of course, two-level or multi-level security isn't workable. At the end of the day, though, we have a working system. One problem is that it is implemented as an old style XUL add-on and so it will not work with the current version of Firefox. There are clear limitations of this "reverse web scraping" approach to automatically managing passwords - not all websites do security in the same way. There is also the issue of allowing Firefox or any browser to be the keeper of the keys. Passwords stored in a browser already make the browser a weak point in security. The only thing that keeps the information safe is the need for physical access to the device and perhaps a master password. This is a good idea, but it would be better to define a protocol that sites can make use of to change the password automatically. This changes the security model to a one-time token. You use the token to gain access to the site and immediately change the password so creating a new access token. The advantage is that the user doesn't have to know what the password is and all of the security concerns are focused on the browser. The only danger is that the current password could still be stolen and used to change the password, so locking the browser out, but at least we have minimized the time period in which this could occur. The bottom line is that we really haven't given the humble password the infrastructure it needs to make it easy to use and effective. More InformationFluid Passwords - Mitigating the effects of password leaks at the user level Related ArticlesGOTCHA - No More Password Hacking Project Wycheproof Reveals Bugs In Popular Crypto Libraries Can AI Change the Face of Cyber Security? Identifying Programmers From Executable Binaries
To be informed about new articles on I Programmer, sign up for our weekly newsletter, subscribe to the RSS feed and follow us on Twitter, Facebook or Linkedin.
Comments
or email your comment to: comments@i-programmer.info
|
| Last Updated ( Friday, 08 September 2017 ) |