| Breaking The Cipher Of Mary Queen Of Scots |
| Written by Lucy Black | |||
| Sunday, 29 June 2025 | |||
|
Researchers who break ciphers for fun have been talking about how they broke the coded letters of Mary Queen of Scots using a combination of computer algorithms, linguistic analysis and manual codebreaking techniques. Mary Queen of Scots is traditionally seen as a tragic victim, and there's plenty to back this up. She became queen of Scotland at six days old when her father James V of Scotland died. She was sent to France to keep her safe from invading English forces, was married to Francis, Dauphin of France, and became Queen Consort when he ascended to the throne.
 Following his death she returned to Scotland, had a son with her second husband, and after her second husband was murdered, (with the murderer rumored to be the man she then married soon afterwards) was forced to abdicate in favor of her young son. She fled to England for protection by her cousin Elizabeth I, who took her prisoner and eventually had her executed because of the worry that supporters of Catholicism were plotting to use Mary to take over the throne of England.
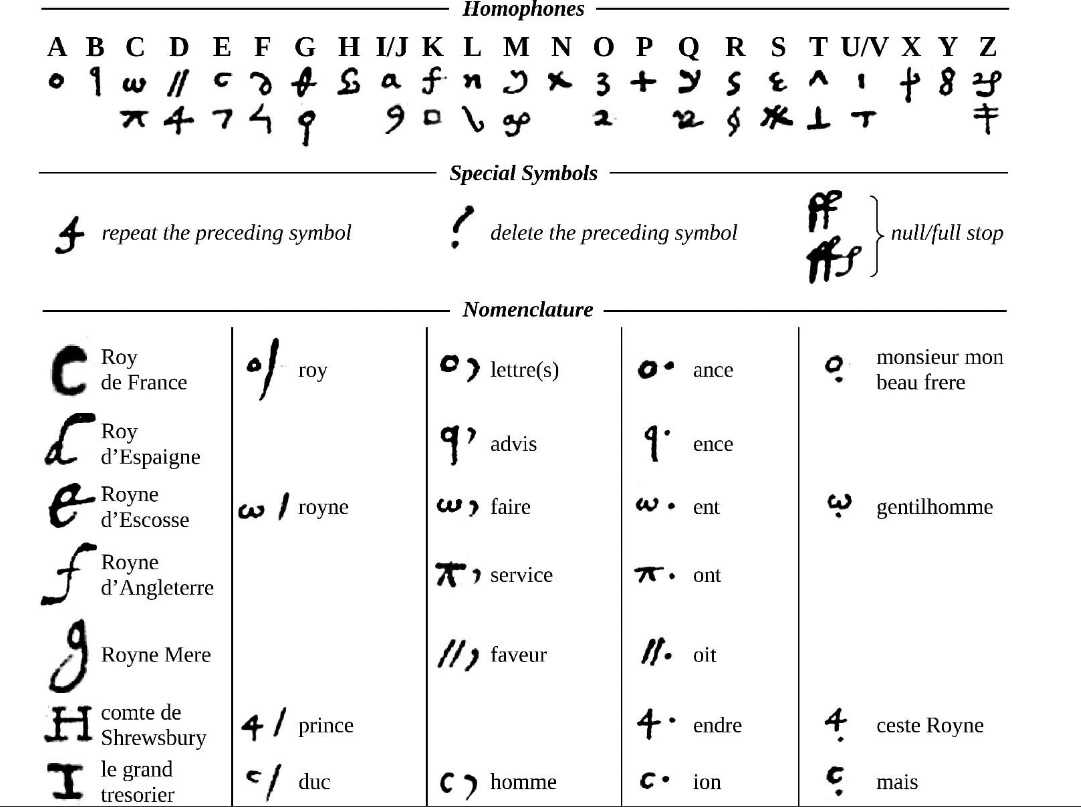
What the researchers have discovered is that Mary was still fighting her corner even when imprisoned by the English. A collection of 57 letters, written in code using a cipher made up of symbols rather than alphabetic characters, was found in the French national library. They were labeled as written in Italian, with no clue that they had anything to do with Mary Queen of Scots or with Elizabethan England.
The team of researchers, made up of George Lasry, an Israeli computer scientist, Satoshi Tomokiyo, a Japanese astrophysicist, and Norbert Biermann, a German music professor, decode ancient ciphers just for fun. They look through archives for unbroken ciphers and try to decode them. This collection was only listed as documents in cipher, and was kept in a larger collection described as originating from the 1520s and 1530s and mostly relating to Italian affairs.
The team used a combination of computerized cryptanalysis, manual codebreaking, and linguistic and contextual analysis. They started by transcribing the documents which contain only graphical symbols into a format readable by software programs. Due to a large amount of material (more than 150,000 symbols in total), the team used CrypTool 2. This is an open source successor to CrypTool 1, which was developed in 1998 at the security department of Deutsche Bank. CrypTool 2 visualizes cryptography and cryptanalysis. It includes the encryption and cryptanalysis of ciphers, along with their basics and information on the whole of modern cryptography.
After transcribing some of the documents, the team performed an initial computer analysis and decipherment. This showed over 200 graphical symbols, some of which would represent single letters, others standing for words or names. The first attempt assumed that the language was Italian, as most of the other documents in the archive collections were in Italian, but that returned no meaningful results. They then tried a reanalysis assuming that the language was French, and obtained a tentative decryption that located multiple modern French words including "prochaine", "beau-frere", "irriter", "persister", "moins", "temps", and "se voir", alongside a number of Middle French words and partial words including "catholi...", "craignan...", and "persecut...".
 From the results obtained using this technique, the team hypothesized that some of the symbols might have the effect of duplicating the last letter instead of representing one of the letters of the alphabet, and of standing for prefixes and suffixes. This task was performed manually, based on linguistic analysis of the deciphered fragments. The team then went on to develop their codebreaking algorithm. In their paper describing their research, the team explain that the principle behind the algorithm is mapping the problem of recovering the key of a cipher only from ciphertext into an optimization problem. To do so, a score is assigned to possible solutions (in this case, possible cipher keys) and a search is performed to find the optimal solution. The size of the problem necessitated the use of stochastic search, a widely used family of techniques to search for the optimal solution more efficiently than with brute force. The specific technique used was hillclimbing, a simple and commonly-used stochastic search technique. To score candidate solutions – in this case, a possible key mapping of the homophones to alphabet letters, the ciphertext is first deciphered using the candidate key, and a score measuring the quality of the deciphered is computed. Hillclimbing starts by generating a random key, i.e., a random mapping of the homophones to the letters of the alphabet. It then iteratively performs small changes in the key, each time deciphering the ciphertext with the modified key, scoring the resulting deciphered text, and if the score is better, the changed key is retained. If the score is worse, the change is discarded. This is continued until there are no improvements. This can result in the algorithm finding an incorrect solution, so it was repeated multiple times with different random starting solutions. Based on the partial decipherment of several documents, the team worked out that the documents were letters written by Mary, Queen of Scots, to Castelnau, the French ambassador to London. This was helped by having a number of letters known to have been written between Mary and Castelnau that matched some that had been deciphered. The known letters had been apparently leaked to Francis Walsingham, Queen Elizabeth I's secretary and spymaster, by a mole in Castelnau's embassy. These decoded letters and their matches enabled the team to determine or validate the meaning of other symbols. They then went on to identify symbols representing names, places, and the twelve months of the year and completed the transcription and decipherment of all the documents.
What the letters show is that Mary was still working to influence events at the English court. In a talk at the Chalke History Festival, team members said that the letters show Mary putting forward things for Castelnau to say to show Mary in a good light or to alter the likelihood of Elizabeth marrying. Mary (and her son James) were in line to inherit the throne if Elizabeth died without children, and in the event Mary's son James became king on Elizabeth's death. The letters tell Castelnau what to say about Mary, and what not to say, in some cases providing the exact words for Castelnau to use. The letters will be released in a book in 2027, and a paper detailing the research is available now. More InformationDeciphering Mary Stuart’s lost letters from 1578-1584 Related ArticlesNIST Announces Post-Quantum Cryptographic Algorithms Levchin Prize for Real-World Cryptography Zodiac Killer code cracked? Cryptography at its worst To be informed about new articles on I Programmer, sign up for our weekly newsletter, subscribe to the RSS feed and follow us on Facebook or Linkedin.
Comments
or email your comment to: comments@i-programmer.info |