| Open Source Insights Into The Software Supply Chain |
| Written by Nikos Vaggalis | |||
| Thursday, 10 June 2021 | |||
|
Open Source Insights is a new project by Google that helps developers understand and visualize their applications' dependencies and therefore the vulnerabilities that come with them. Supply chain security is all the rage right now. We've taken a look at the implications as well as the ways of mitigation in "Does Sigstore Really Secure The Supply Chain?" the Linux Foundation's answer to supply chain attacks: To build useful software we don't reinvent the wheel but we base on work already done coming bundled in the form of libraries.The problem is that even a mediocre open source project can have loads of such dependencies which themselves depend on others, forming a lengthy chain.Not a problem per se unless malicious code or security vulnerability finds its way anywhere in this chain. A way of strengthening against it is by in integrating security in the software's development life cycle rather than treating it as an aftermath. As I've detailed in "The State Of Secure Software Development", this approach involves a security mindset as part of the CI/CD pipeline, SAST tools application,vulnerability scanning and dependency audits.
But sometimes even those counter measures can't keep up with the radical ways that software updates itself. A tool that would let you get down to the bottom of every dependency as large or as little that might be, would be a great addition to one's security oriented arsenal;project Open Source Insights, under the auspices of Google Open Source, comes to fill that void. It is capable of detailing how a particular software package is put together;how its building blocks depend on each other. The service crawls github.com, npmjs.com, and pkg.go.dev , extracts the necessary information and metadata from the software packages and then builds a full dependency graph.It is not static as it continually updates it results, thus even allowing for comparing versions between each other.
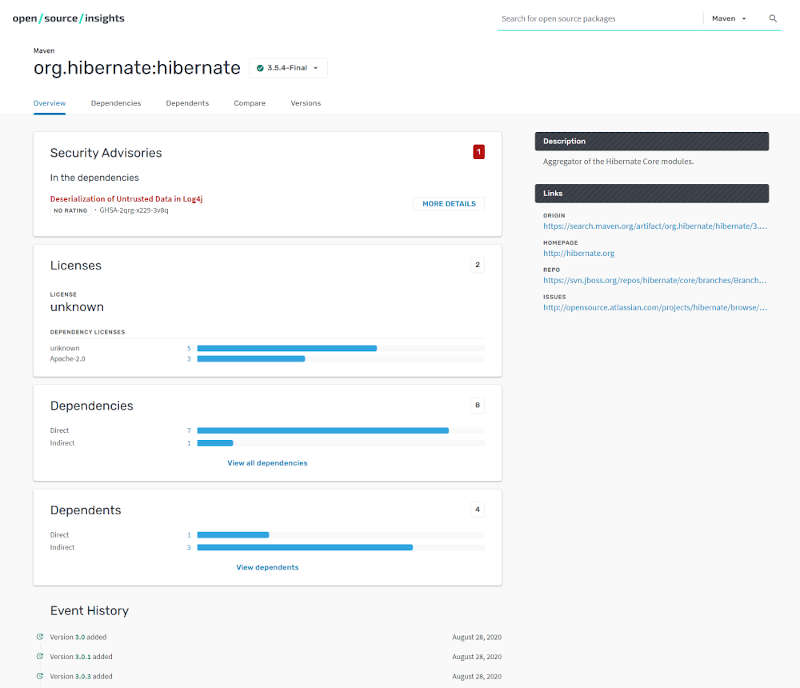
For instance looking for org.hibernate:hibernate, we get the overview of the package which comprises of:
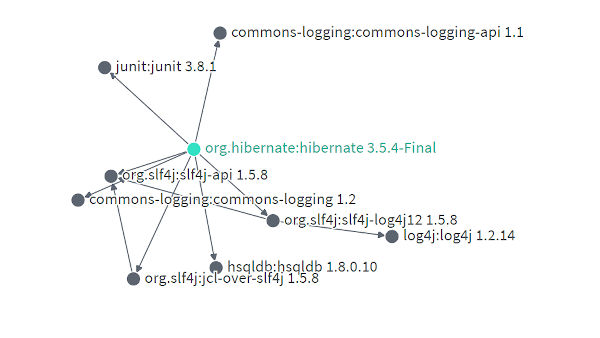
Dependencies and Dependents (the projects that depend on the package) are further analyzed on their own sections,and can be even visualized as a graph.Further, under the Comparison section you find what has changed from one version to the other.Suffice to say that with each dependency path you follow the further down the rabbit hole you descent... In these times that OSS is more ubiquitous than ever, such insights can be proven very valuable. Available on https://deps.dev/ More InformationRelated ArticlesThe State Of Secure Software Development - Three OpenSSF Courses Does Sigstore Really Secure The Supply Chain?
To be informed about new articles on I Programmer, sign up for our weekly newsletter, subscribe to the RSS feed and follow us on Twitter, Facebook or Linkedin.
Comments
or email your comment to: comments@i-programmer.info |
|||
| Last Updated ( Thursday, 10 June 2021 ) |