| $200,000 Competition To Break Telegram's Code |
| Written by Kay Ewbank | |||
| Friday, 20 December 2013 | |||
|
Can you crack Telegram's encryption? If so you could win $200,000 but you have to do it before March next year and it looks like a difficult task. Updated The open-source private messaging service Telegram has launched a competition to show off its encryption technology. The challenge is that the first person to break the protocol will win $200,000 in Bitcoins. How much the prize will be worth after a few minutes of being awarded is another matter!
Telegram is a relatively new company started in August 2013 by the founders of VKontakte, the largest European social network, and the prize money for the competition is being provided by VKontakte founder Pavel Durov. The way the competition works is that each day Paul (+79112317383) will be sending a message containing a secret email address to Nick (+79218944725). To win the prize, you need to decipher the message, find the secret email address, and send an email to it. Your email has to contain the entire text of the message that contained the secret email, your Bitcoin address to receive the $200,000 in BTC, and a detailed explanation of how you attacked and cracked the encryption.
In the announcement of the competition the Telegram team says that “to prove that the competition was fair, we will publish the participating keys necessary to decrypt the traffic as soon as a winner is announced. In case there is no winner by March 1, 2014, encryption keys will be published at that date.” Telegram is a cloud-based encrypted messaging service that lets you send messages, photos and videos to people who are in your phone contacts. It lets you access your messages from different devices and store an unlimited number of photos and videos in the cloud. The service is free and has no ads. Asked how they intent to make money from the project, the company says “We believe in fast and secure messaging that is also 100% free. Therefore Telegram is not a commercial project. It is not intended to sell ads, bring revenue or accept outside investment. If Telegram runs out of money, we'll invite our users to donate or add non-essential paid options.” VKontakte founder Nikolai Durov developed a custom data protocol that Telegraph says is open, secure and optimized for work with multiple data-centers.
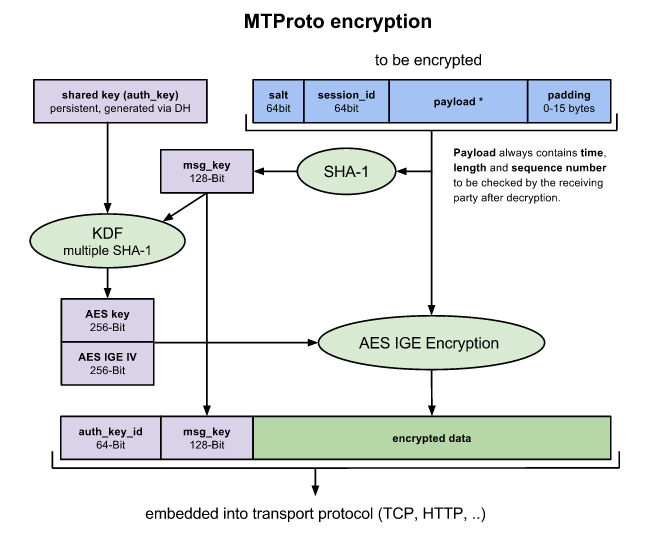
Telegram for iPhone was launched on August 14, 2013, and an alpha version of Telegram for Android was launched on October 20, 2013. Mac OS X and Windows versions are under development by independent developers using The company has an open API for developers that can be used to build applications for other platforms. If you look through the documentation you will discover that the encryption uses AES with a 256 bit key with some additional steps to make it more secure:
Given that AES 256 is still believed (rumours about the NSA aren't confirmed) to be uncrackable then the only real hope is that there is some flaw in the surrounding algorithmic steps involving the keys and the IGE. UpdateAn analysis on the CryptoFails website of Telegram's challenge and its methods suggest that the encryption might not be as secure as it seems. To quote: Some problems are immediately apparent:
If their protocol is secure, it is so by accident, not because of good design. They claim the protocol was designed by “six ACM champions” and “Ph.Ds in math.” Quite frankly, the protocol looks like it was made by an amateur. The tight coupling between primitives suggests the designer was not familiar with basic constructs, like authenticated encryption, that you can find in any cryptography textbook. Even so given that you can't use a known plaintext to challenge the encryption it is still a difficult task. If the cypher isn't cracked in the time it doesn't prove that it is secure only that it is secure under the restricted conditions of the competition.
More InformationTelegram’s Cryptanalysis Contest Related ArticlesStick Figure Guide To AES Encryption Public Key Cryptography Set To Fail In Five Years Open Source Homomorphic Cryptography Web Crypto APIs Work In Progress
To be informed about new articles on I Programmer, install the I Programmer Toolbar, subscribe to the RSS feed, follow us on, Twitter, Facebook, Google+ or Linkedin, or sign up for our weekly newsletter.
Comments
or email your comment to: comments@i-programmer.info
|
|||
| Last Updated ( Friday, 20 December 2013 ) |