| Copied Code Is Vulnerable Code |
| Written by Alex Armstrong | |||
| Wednesday, 09 October 2019 | |||
|
We all look up code online and then modify it and incorporate it into our programs, but is this a safe practice? New research suggests that it most definitely isn't. Code reuse from forums, notably Stack Overflow, is a productivity boon, but there are lots of questions about the quality of the code. Most of it isn't production quality - that is obvious as it is created simply in an effort to answer some small point raised in a question, but surely nothing bad could happen by simply using it? Researchers from Shiraz University (Iran), Montreal University (Canada) and Chamran University (Iran) decided to look at C++ code and see if it contained any vulnerabilities - it did. In a data-set of 72,483 C++ code snippets used in at least one GitHub project, they found 69 vulnerabilities and 29 different types of vulnerability. What is equally worrying is that the 69 vulnerable code snippets were found in 2589 GitHub files. The most common vulnerability transferred from Stack Overflow was CWE-150: "The software receives input from an upstream component, but it does not neutralize or incorrectly neutralizes special elements that could be interpreted as escape, meta, or control character sequences when they are sent to a downstream component." Here is an example of the code that was flagged as vulnerable: void gen_random(char *s, const int len) {
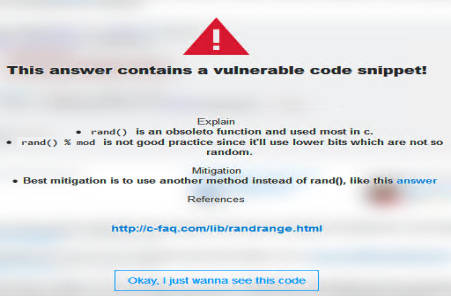
You can probably spot the problems - if len is the length of the string not including a null, then setting it to zero is an overrun; and if the string is null terminated why pass len and why set it to null? Less obvious is that rand is obsolete and taking the mod returns the lower bits, which are not very random. What is really surprising is that this code snippet was re-used as there are various critical comments following it that indicates that it isn't good. In particular: We need a way to sink obsolete answers on stackoverflow. – Velkan May 23 '17 at 6:20 When using a code snippet there is a lot to think about. Presumably if the programmer was on top of the problem they wouldn't have searched out a potted solution and for them to validate the code they would have to understand it at a fairly deep level. To help with this problem the researchers have created a browser extension that marks answers that have vulnerable code:
There are lots of other interesting examples and ideas in the original paper but it also contains errors and typos - it is a first draft. More InformationAn Empirical Study of C++ Vulnerabilities in Crowd-Sourced Code Examples Morteza Verdi, Ashkan Sami, Jafar Akhondali, Foutse Khomh, Gias Uddin and Alireza Karami Motlagh Related ArticlesNever Mind The Code Quality ... Stack Overflow: A Code Laundering Platform? Do You Have To Attribute Stack Overflow Code? Can a Language Make You a Better Programmer? Kotlin & Android To be informed about new articles on I Programmer, sign up for our weekly newsletter, subscribe to the RSS feed and follow us on Twitter, Facebook or Linkedin.
Comments
or email your comment to: comments@i-programmer.info |
|||
| Last Updated ( Wednesday, 09 October 2019 ) |