| How WiFi Works |
| Written by Harry Fairhead | |||
| Saturday, 29 October 2022 | |||
Page 2 of 2
Ad-hoc and infrastructure modesAs well as the radio link part of wireless networking there is also the problem of how to integrate a wireless network with a wired network. There are two basic modes of operation – ad-hoc and structured. A group of computers that can communicate using a wireless link are called a Basic Service Set, or BSS. An ad-hoc network also known as an Independent Basic Service Set (IBSS) is the simplest because all of the machines communicate with one another in a peer-to-peer or workgroup network. When two or more IBSS operate as a single workgroup the result is called an Extended Service Set, ESS. The alternative is Infrastructure mode, which makes use of special Access Point (AP) wireless device. This is a stand-alone box that only needs a network connection and not a PC to operate. The AP acts as a master and controls all transmission within a BSS. It has management algorithms and transmits special control packets to its clients to make best use of the available bandwidth. The AP also connects to a wired network and acts as a wireless/wired bridge passing data packets in both directions. Two APs never talk to each other via the wireless link and always transfer data between themselves via the wired network. As well as allowing wireless connected machines to integrate with a wired network, an AP also provides extra facilities such as broadcasting the network identifier, the Service Set Identifier (SSI), allowing users to discover that a network is available. An AP also enables “roaming”. That is, if a user moves around from one BSS to another, as long as the access points are using the same SSI then the user will be automatically handed over as one AP goes out of range and another comes into range. Infrastructure mode is so much better than ad-hoc that some wireless networking cards can act as APs, even though they aren’t standalone and need a PC to operate. SecurityA wireless network has all of the security problems of a wired network plus the additional drawback that it broadcasts the data packets rather than keeping them safe inside the wires. Extra security in the form of Wired Equivalent Privacy (WEP) was designed into all of the standards to, as its name suggests, make a wireless network as secure as a wired network. Unfortunately this is one area where the standards got it wrong. The first problem is that WEP is turned off by default and even though it’s flawed it’s better than nothing. The second problem is that it is often based on using a very short cryptographic key and the RC4 cipher algorithm. It works by using a secret key, a 64-bit number, and using it to create a seemingly random stream of bits – the key stream. The key stream is combined (Exclusive ORed) with the data before it is transmitted. When it is received the same key is used to generate the same key stream and this is used to recover the data.
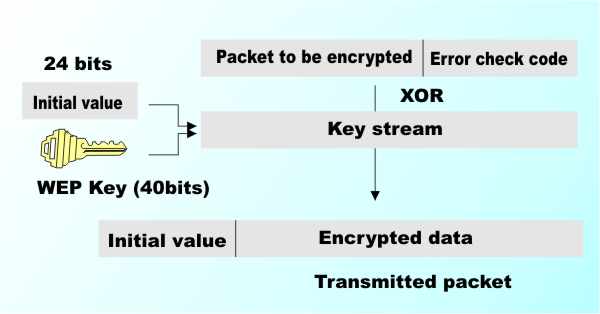
How WEP works
The 64-bit key is obtained by combining a 40-bit WEP key with a random 24-bit initialisation value. The initialisation value is transmitted with the packet and is unencrypted. As long as the receiver has access to the same 40-bit WEP key then the initialisation value can be used a second time to recover the 64-bit key and decode the data. What is wrong with WEP?The fact that it uses only a 40-bit key makes it possible to decrypt using brute force. Most modern wireless cards and software supports larger keys but this doesn’t help with the next two problems. The initialisation value is only 24 bits long and this means that is reused too often, giving an attacker samples of packets encrypted using the same value. When you add to this the fact that some values are particularly easy to crack you can see why it isn’t a good method. Finally the WEP key is a “shared secret”. That is, it has to be distributed to each network user by some method or other. Distributing keys is a weakness in itself. WPA, WPA 2 and 802.11iThe only way around the problem is to use additional security. A collection of stopgap measures called Wi-Fi Protected Access (WPA) is currently the best we have. Add to it TKIP, which uses dynamic WEP keys, to stop eavesdroppers guessing the key and public key cryptography to distribute the WEP keys over the wireless network an it works quite well. However another standard – 802.11i or WPA 2 – is an even better solution. Clearly WPA is better than WEP but surveys have revealed that the majority of wireless networks don’t even use WEP and it’s important to realise that in this case the data is being transmitted unencrypted and can be read by anyone with a portable computer, a wireless network card and some purpose-built software. What is more open networks can be used by anyone and you could find yourself liable for what they download with no way to prove it wasn't you.
Related ArticlesTo be informed about new articles on I Programmer, sign up for our weekly newsletter, subscribe to the RSS feed and follow us on Twitter, Facebook or Linkedin.
Comments
or email your comment to: comments@i-programmer.info |
|||
| Last Updated ( Saturday, 29 October 2022 ) |