| Simple Runtime Framework by Example |
| Written by Alexey Lyashko | |||||
| Wednesday, 06 June 2012 | |||||
Page 2 of 2
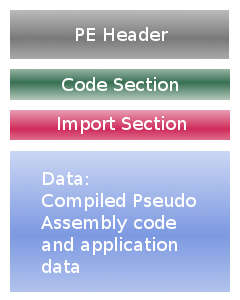
In the case of .NET framework (at least as far as I know), the loader identifies a file as a .NET executable, reads in the meta header, and initializes the mscoree.dll appropriately. We will not go through all those complications and will use a regular PE file:
Example Executable Source CodeThe following is the source code of the example executable. It may be compiled with FASM (Flat Assembler).
The code above produces a tiny executable which invokes framework's core() function. Pseudo assembly code simply prints two messages (the first one is decoded prior to being printed). Full source code is available, see link at the end of the article. The good thing is that you do not have to start the interpreter and load this executable (or specify it as a command line parameter) - you may simply run this executable, Windows loader will bind it with the framework.dll automatically. The bad thing is that you would, most probably, have to write your own compiler, because writing assembly is fun, dealing with pseudo assembly is fun as well, BUT, only when done for fun. It is not as pleasant when dealing with production code. Possible usesUnless you are trying to create a framework that would improve on existing software frameworks, you could use such approach to increase the protection of your applications by, for example, virtualizing cryptography algorithms or any other part of your program which is not crucial in terms of execution speed, but represents a sensitive intellectual property.
Source code for this article may be found here.
This article originally appeared on Alexey Lyashko's blog System Programming and is reproduced here with kind permission of the author. Related ArticlesTo be informed about new articles on I Programmer, install the I Programmer Toolbar, subscribe to the RSS feed, follow us on, Twitter, Facebook, Google+ or Linkedin, or sign up for our weekly newsletter.
Comments
or email your comment to: comments@i-programmer.info |
|||||
| Last Updated ( Wednesday, 06 June 2012 ) |