| PowerHammer - Leaking Data Through The Power Line |
| Written by Harry Fairhead | |||
| Sunday, 15 April 2018 | |||
|
One of the things you just have to accept is that human ingenuity will always find a way. When it comes to security even the strongest protection will fail. An air-gapped computer has no external networking connections so it cannot leak data to the outside world. Don't you believe it. The highest security machine is generally referred to as being "air-gapped". The idea is that there are no network connections to the machine and there is indeed a gap of air between it and every computer in the world. Of course, faced with such a challenge people are bound to find ways to get data out of an air gapped machine and a team at the Cyber Security Labs of Ben-Gurion University, Mordechai Guri, Boris Zadov, Dima Bykhovsky and Yuval Elovici, have made it their specalist subject. Their latest method makes use of the fact that an air-gapped computer isn't really air-gapped at all - there has to be a power cord and this connects the computer to the outside world. What harm can a mains power connection do? The answer is that all you have to do is measure the current being drawn by the connected machine and use it as a covert data channel. In nearly all cases the modern machine is very power-efficient and uses a switch mode power supply that matches the power demand moment by moment. You might think that the power drawn by a computer would be a constant - like a heater or a lamp - but this isn't the case. The CPU takes an amount of power that varies according to what it is doing. When it is flat out computing it takes maximum power and when it is doing nothing it takes significantly less power. This power variation has to be passed on through the power supply to the mains power feed. There is no way of knowing that this could be used as a signal. The change in the current might be too small to be detected among the variations caused by other components varying their current draw. It might be that the power supply has smoothing components that even out rapid changes in current and effectively form a low-pass filter. However, in the case of the machines that the researchers tried, the signal was definitely detectable.
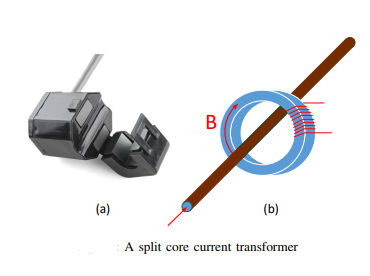
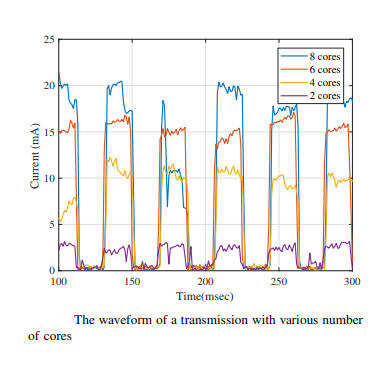
In the main example, 2 cores of a 4-core processor were used to send a signal. A carrier frequency was generated and frequency shift modulation used. The use of a carrier frequency made it more likely that the receiver would be able to pick the signal from the noise. The current variations were picked up using a non-contact current transformer. Such devices are available off the shelf and measure current without needing a direct connection to the power cable - you simply clamp the cable in the jaws of the device. The current signal was converted to digital measurements and processed using software. In a more covert set up it would be possible to build hardware that was small and difficult to spot to do the same job. It proved perfectly possible to transmit reliably at up up to 1000 bits per second on a standard PC, but this was only 100 bits per second on a server and 5 bits per second with 1.9% error on a Raspberry Pi. Clearly the success of the attack depends on the machine. It is also clear that the signal becomes stronger the more cores are used to create the carrier signal. In the case of the PC, 2 cores produced a current variation of 2.5mA and 4 cores produced 12mA and so on.
This initial attack was with the sensor placed on the direct power feed to the machine - although some distance away. A second attempt was made, but this time putting the current sensing device in the distribution cabinet. The problem here is that many other devices are also causing variations in the current with the result that there is a lot more noise. However, it still worked, but with a much reduced data rate The PC managed 3 bits per second with no errors.
What can be done to stop the power consumption being used as a signaling method? The researchers suggest that the only options are detecting the signal, putting filters in the power line, detecting the software in the machine and generating a jamming signal. A much easier solution would be to use a completely isolated UPS - one that runs the machine from a battery 100% of the time and keeps the battery topped up with a steady current that doesn't vary with the machine's demand. This is the ultimate low-pass filter! More InformationPowerHammer: Exfiltrating Data from Air-Gapped Computers through Power Lines Related ArticlesDisk LEDs Leak Data & So Do Phone Magnetometers Your Android Could Leak Data Via USB Charging SilentKeys A Privacy Aware Keyboard Identifying Programmers From Executable Binaries Your Phone's Battery Leaks - Your Id That Is WebRTC Leaks Local IP Addresses Cat Photos - A Potential Security Risk? Print Me If You Dare - the Rise of Printer Malware Security by obscurity - a new theory To be informed about new articles on I Programmer, sign up for our weekly newsletter, subscribe to the RSS feed and follow us on Facebook or Linkedin.
Comments
or email your comment to: comments@i-programmer.info |
|||
| Last Updated ( Sunday, 15 April 2018 ) |